Linux has gained a good name for being secure enough, and resistant to many malwares out there. Some of the popular Linux based operating systems are Ubuntu, Mint, Fedora, Redhat, Debian, Arch. Nevertheless, none of these operating systems by default utilize a proper antivirus guard. So this article takes this belief under scrutiny, and see whether a Linux based operating systems really requires an anti-virus guard or not.
What is a Linux System?
Even though in popular culture all the Linux operating systems are banded together and regarded as one, the reality is Linux is just a kernel, which is the base of many operating systems that utilize the aforesaid kernel. Some of the popular Linux based operating systems, also known as flavors are Ubuntu, Mint, Fedora, Redhat, Debian, Arch. Each one serves a purpose, and has a large dedicated faithful community around it, also some Linux operating systems like Ubuntu has multiple types such as Desktop, Server in order to cater for certain groups.
That being said, regardless of the flavor, the desktop version is usually tailored to regular users, and therefore it has a graphical user interface, whereas the server type is tailored to cater for IT personnel who usually mastered shell commands; hence by default they lack a graphical user interface.
Structure of Linux Operating System
Any Linux operating system regardless of its flavor has multiple user accounts. By default, the supreme user in Linux is root, which is not recommended to use for general purposes due to the risks associated with it, and therefore when the operating system is installed it prompts to create a new user account with limited privileges. These privileges confine the jurisdiction of the particular user account; hence it’s less likely the whole system is affected in case of the security of the operating system is compromised.
All the processes by default run under the currently logged in user account instead of as the root user. All the users are given a separate folder in the base location of the file system, which is known as “Home”, and if the currently logged in user account is breached, only this folder is affected.
Malware and Types
A typical anti-virus guard provides protection from not just viruses, but also a range of malwares existing out there. Some of the popular malware types are adware, spyware, virus, worm, Trojan, rootkit, backdoors, key loggers, ransomware, browser hijacker. That being said, the general public often refers all these malware as viruses, even though a computer virus is a piece of code attached to a standalone application, and is executed when its host is executed. Linux seems immune to certain malware types, but it doesn’t necessarily mean it’s immune to attacks from all the malware types, for instance a spyware serves a purpose in spying on users. Since it’s fairly easy to run any application on user level, a spyware can easily penetrate the system and keep spying on the user, same goes for adware, worm, Trojan, backdoors, key loggers, and also ransomware. So, this misconception of not having any threats in Linux is obviously a fallacy. The risk is still there, but it’s far lower compared to the Windows family of operating systems.
What an Antivirus Guard does?
Anti-virus guard applications perform various actions from scanning files to quarantining found threats. Usually any an anti-virus guard keeps a database that consists of signatures of the known viruses. When anti-virus scans a file for threats, it hashes the file, and compares it against the values existing in its database, if both are matched, the file is quarantined. This signature database is often updated by default unless it’s disabled manually to give a consistent protection.
Why Linux Needs an anti-virus guard?
Some systems consist of mail relay, web server, SSH daemon, or ftp server which are very likely to require more protection than an average desktop operating system that is hardly shared by multiple people. Other server systems exist deep beyond firewall for computations and are rarely accessed by many people, or changes to new applications and are at low risk for being infected.
In popular Linux flavors like Mint and Ubuntu there is an inbuilt package which is connected with the official software repository from where applications can be downloaded to Install. Since this repository is under the scrutiny of thousands of volunteers, and developers, it’s less likely it contains of malware.
However, there is a risk if software is downloaded through a different source, for instance apart from downloading the software through the official repository, many Linux distributions allow users to download software through various PPA (personal package archives), if a software is downloaded through such a source, and if it contains any harmful content, there is a risk the computer is compromised depending on how the malware is coded and for what purpose it’s designed. So, if third party PPAs are often used, it’s a wise decision to install an anti-virus guard to keep the system safe.
A popular free anti-virus guard to secure a Linux system is Comodo Antivirus for Linux. It not only protects the file system, but also the mail gateway from unauthorized accesses. This is specifically designed for regular desktop users to keep the system secure and safe.
As stated earlier, even though a malware can’t gain full access to the whole operating system, it can still gain access to the user level. Having user level access is still dangerous, for instance using this command rm -rf $HOME can completely wipe out the home directory of the user and make their day miserable. If there wasn’t a backup of the home directory, the damage can be tremendous. Also, nowadays a popular widespread threat is ransomware, which encrypts the entire hard drive and demands a payment via bitcoins in order to decrypt the files. In such cases, even though it can’t penetrate the system, it can still encrypt the home directory, and make the user completely helpless. The home directory stores pictures, documents, music, videos, and getting these folders encrypted means a big loss to the user. Since criminals often demand a huge payment from victims, unless the user is rich, getting the files unlocked is very unlikely. So it’s better to install an antivirus guard to keep the system secure than being a victim of a petty criminal.
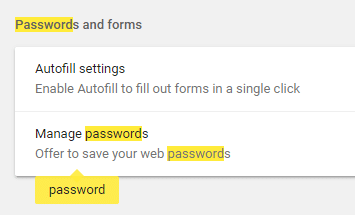
Other threats to desktop Linux systems are browser hijackers, adware. These applications are often installed via the web browser, and so even if the operating system is secure, the web browser is vulnerable to such threats. This leads the passwords to be leaked, and constant ads to pop up randomly in websites. So it’s important for web browser to use a master password to secure the passwords typed through it. The following screenshot demonstrates the option for managing the passwords typed through Google chrome. When there isn’t a master password to secure these passwords, a malicious extension/plugin installed in the browser can easily extract them. This is more dangerous on Firefox than Chrome, as Firefox doesn’t have a master password by default, Chrome, on the other hand, requests to type the password of the user account of the operating system in order to display them.
Furthermore, Linux servers require a better safeguard in order to keep its main services secure. Some of such services are mail relay, web server, SSH daemon, ftp server. Since a server uses so many services which interact with the public, the result may be catastrophic.
A good example for this is a public server which hosts windows software gets infected with a malware, and spreads harmful contents to multiple computers. Since the Malware is written for Windows computers, the Linux server doesn’t take any damage, but it helps to damage Windows computers inadvertently. This seriously damages the reputation of the company that hosts the software.
Likewise, other services also need some kind of a safeguard. Mail relays are often penetrated by malware to spread spams across the Internet. A good solution for this problem is using a third party mail relay instead of maintaining an in-house one. Some of popular mail relays are Mailgun, SendPluse, MailJet, Pepipost. These services provide a better protection against spam, and spreading of malware through Mail relays.
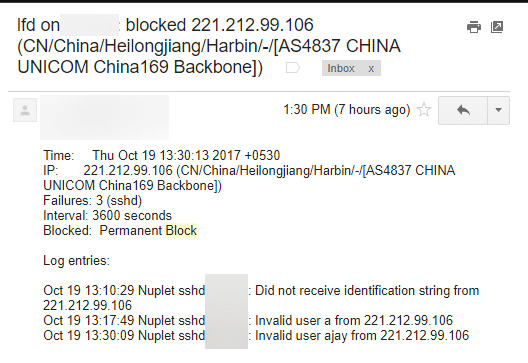
Another service that is susceptible to attacks is the SSH daemon. SSH daemon is used to connect to a server over an unsecure network, and can be used to get the full access to the whole server, including the root. The following screenshot shows an attack to the SSH daemon over Internet coming from a hacker.
These kinds of attacks are quite prevalent to public servers, and therefore it’s extremely important to secure the server from these kinds of attacks. The purpose of unauthorized requests to SSH daemon is getting the access to the server to spread malware, uses it as a node to launch DDOS attack against a different server, or spreads illegal contents.
To secure the SSH daemon CSF (Configured Server Firewall) can be installed along with LFD (login failure daemon). This limits the number of attempts to the SSH daemon, once the limit is over, the sender is permanently blacklisted and their information is sent to the server administrator if it’s configured properly.
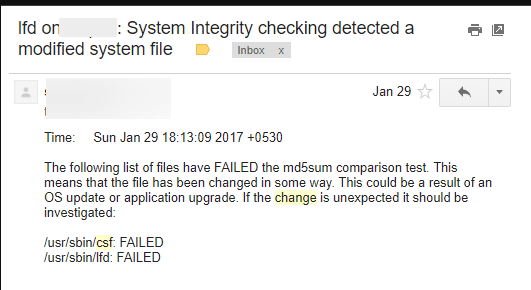
Moreover, CSF tracks the modifications of files, and informs the administrator as seen in the following screenshot. This is quite useful if a package installed via a third party PPA is suspicious. Then, if the package updates itself, or if it changes any file without user permission CSF automatically notifies the server administrator regarding the changes.
The following shell commands install the CSF along with LFD in Ubuntu/Debian Systems.
wget http://download.configserver.com/csf.tgz tar -xzf csf.tgz cd csf sh install.sh
Another big threat to both server and desktop versions is getting the ports unlocked internally. Either a Trojan or a backdoor carries out these operations. With a proper firewall, ports can be opened and closed, so if somehow a backdoor is installed in the system, the closed ports can be opened internally to make the server vulnerable to external attacks.
Why Linux Doesn’t Need an Anti-Virus Guard?
Linux doesn’t necessarily need an anti-virus guard if it’s maintained properly, and software is downloaded through secure channels. Many popular Linux flavors such as Mint, and Ubuntu have their own repositories. These repositories are under strict scrutiny, and therefore it’s less likely a malware to exist in packages downloaded through it.
Also Ubuntu by default has AppArmor which confines the actions of software to make sure they are only performed what they are assigned. Another popular kernel level security module is SELinux which does the same job but in much lower level.
Linux isn’t popular among regular users, and regular users are often targeted by malware due to the fact that they are easier to be manipulated and tricked. So malware writers are pushed to move to the Windows platform instead of wasting time on Linux, which has a lower demographics that can be fooled. So this makes Linux have a secure environment, and so, even if unsecure channels are used to download software, the chance of having a malware is minimum to low.
Conclusion
Security is important for any computer system; this is same for Linux. Even though the popular belief is Linux is completely safe from malware attacks, the number of scenarios pointed out above demonstrates otherwise. The risk gets higher when the computer is shared among multiple people, or if it’s a server to which the public can access over the Internet. So it’s important to take proper safety precautions to prevent catastrophic incidents. This includes installing a proper antivirus guard, a firewall, using a master password to the browser to secure passwords typed through it, using a kernel level module to confine actions of applications if the security is very important, downloading software only through reliable and secure channels like official repositories instead of downloading them through third party or unsecure channels, keeping the operating system up-to-date and always pay attention to latest news and trends posted in various Linux news networks. So in a nutshell Linux doesn’t need an anti-virus guard, but it’s better to have anti-virus guard to make sure the security isn’t compromised.