GPG (Gnu Privacy Guard) is an Open source implementation of Open PGP (Pretty Good Privacy) asymmetric encryption protocol. It generates a key pair of Public and Private keys to encrypt and decrypt your files. Public keys are generally used to encrypt file and they cannot decrypt. On the other hand, Private keys can only decrypt encrypted files. Private keys are also encrypted with symmetric encryption to keep them secure.
Usage
If you’re Kali or Parrot Security OS user, then “gpg” will most probably be pre-installed. If you’re using some other distro then you can install it by typing
user@user:~$ sudo apt-get install gpg -y
Now generate a key pair
root@user:~$ gpg –full-gen-key
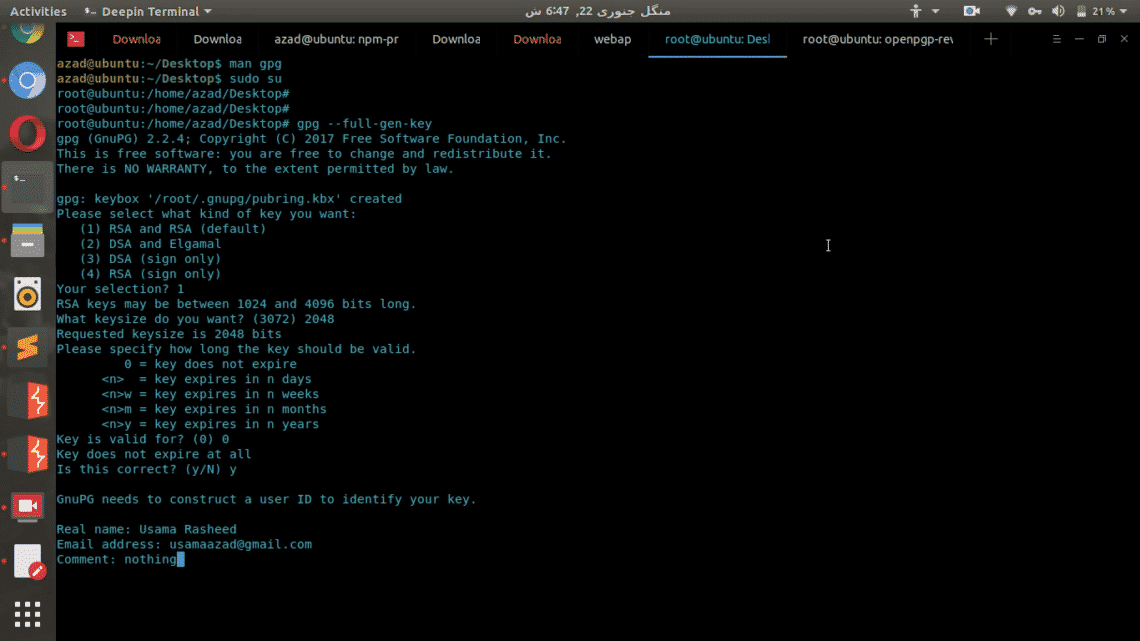
It’ll ask you to select key type, you can choose whatever you want. Then it’ll ask you to enter the size, the longer size you enter, the longer it’ll take to generate the keys but then generated keys will be more secure than others. You can also set the expiry date for your keys and their description in comments.
After these prompts, it’ll ask you for a passphrase. This passphrase will be used to encrypt your private keys using symmetric encryption, so even if your private keys are stolen, no body can use them to decrypt your files.
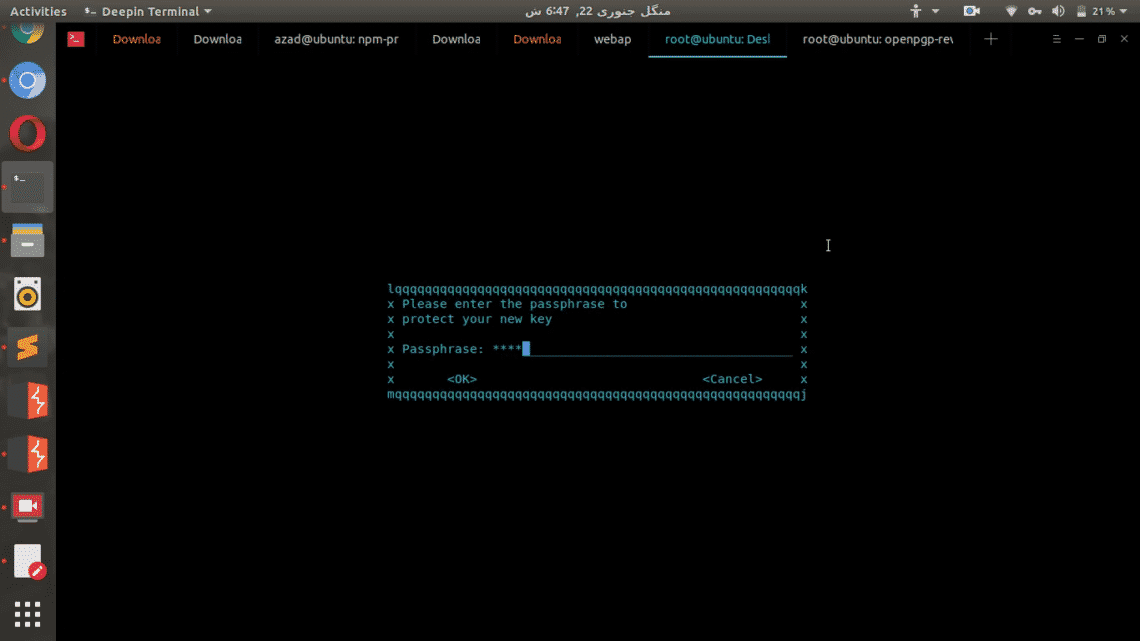
It’ll ask you to re-enter the passphrase, then after pressing enter it’ll take a while to generate the key pair.
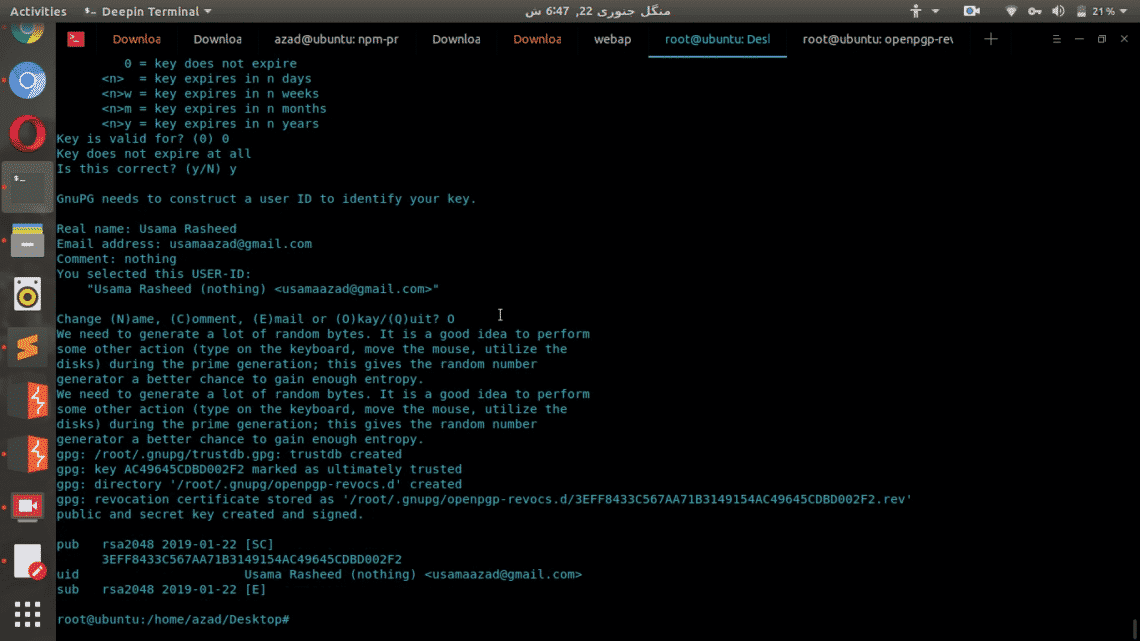
Encryption
Now Public & Private key pair is generated, and you can use this to encrypt and decrypt your files. We’ll create a test file to encrypt and decrypt using gpg.
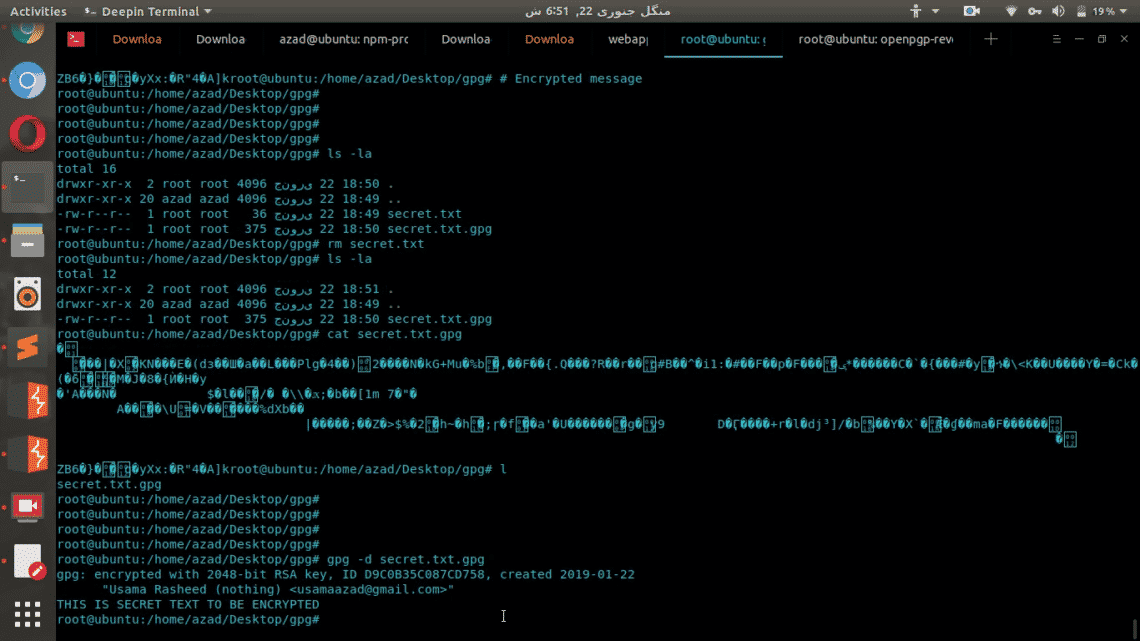
root@user:~/gpg# cd gpg/
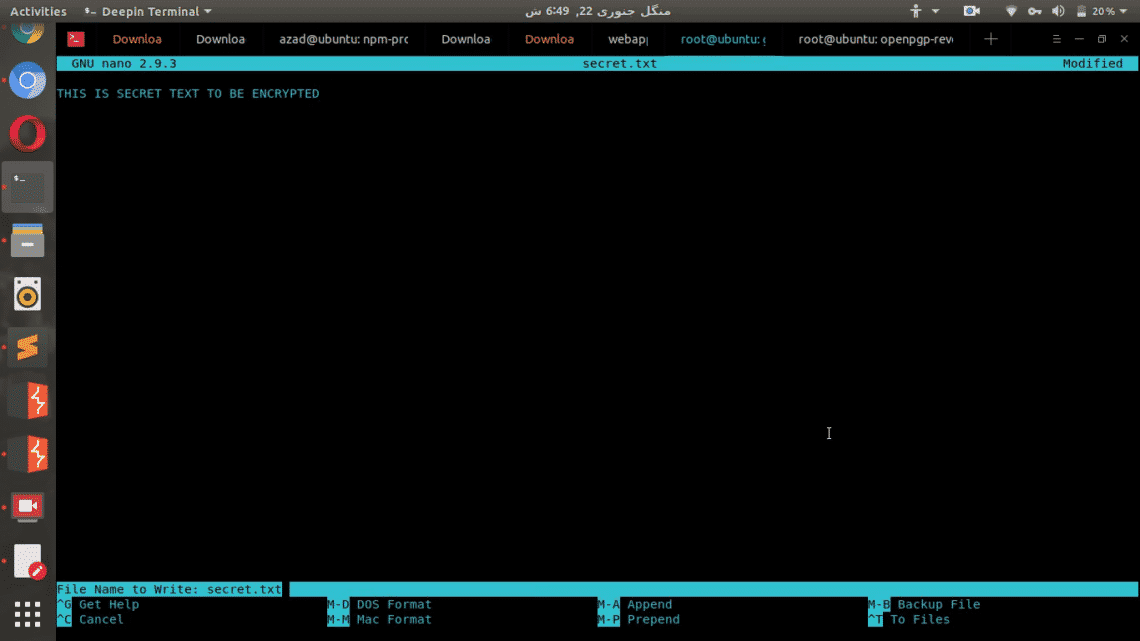
root@user:~/gpg# nano secret.txt
Now enter anything into the text file
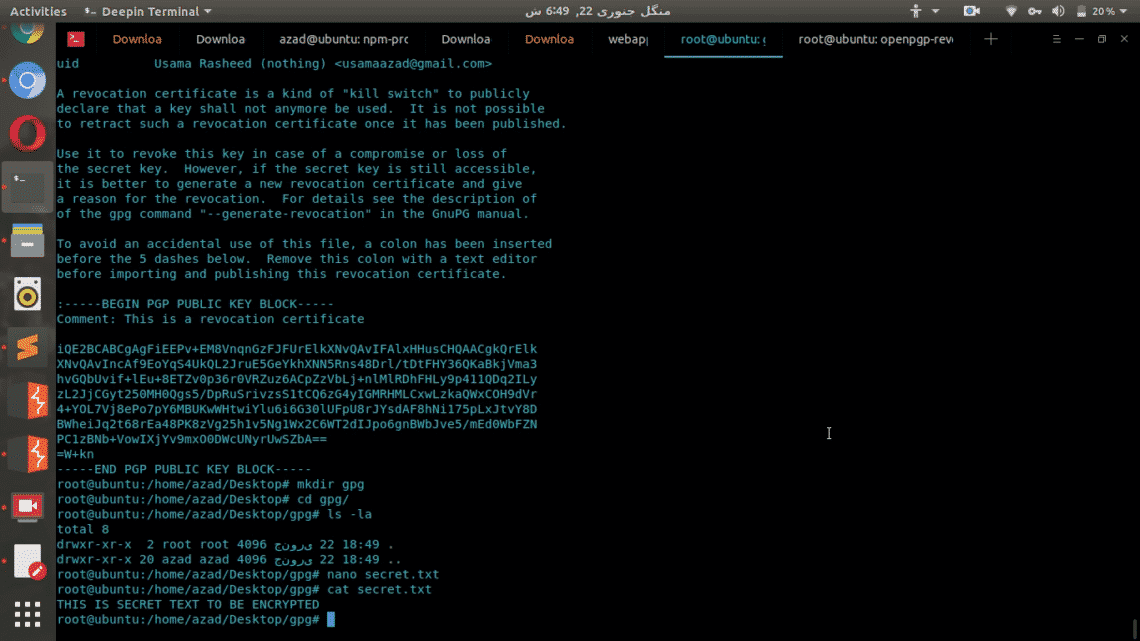
Now encrypt the “secret.txt” file by specifying the user email in generated key pair. Type the following, in my example
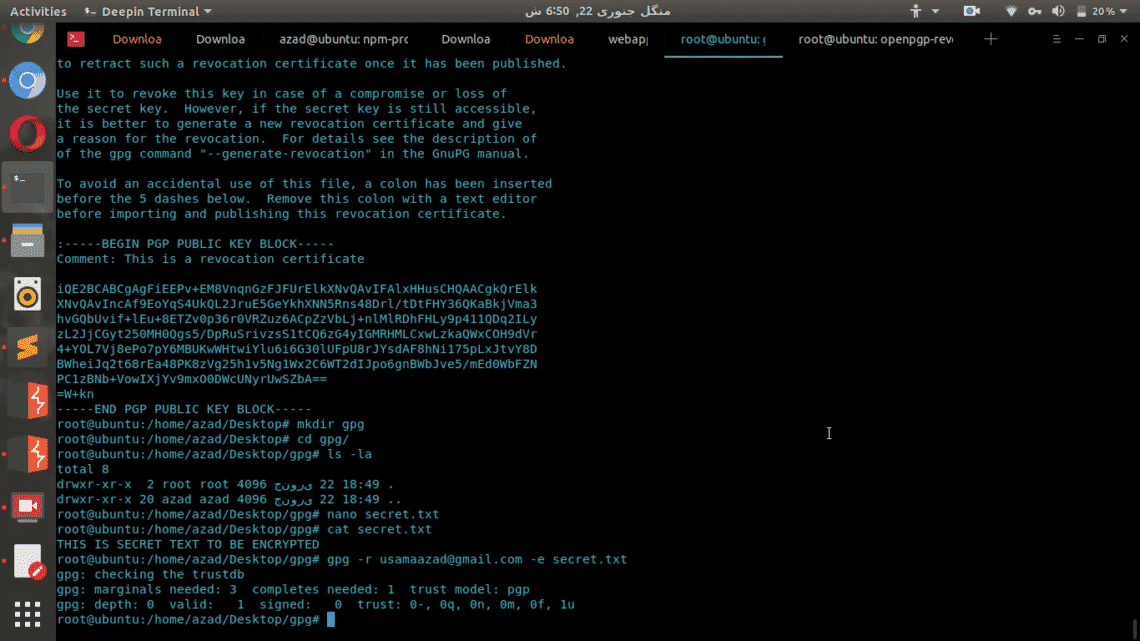
An encrypted file with extension “.gpg” will be generated in the folder. That file is encrypted and secured using your Public key of your key pair. This file now only be decrypted by using your private key.
root@user:~/gpg# cat secret.txt.gpg
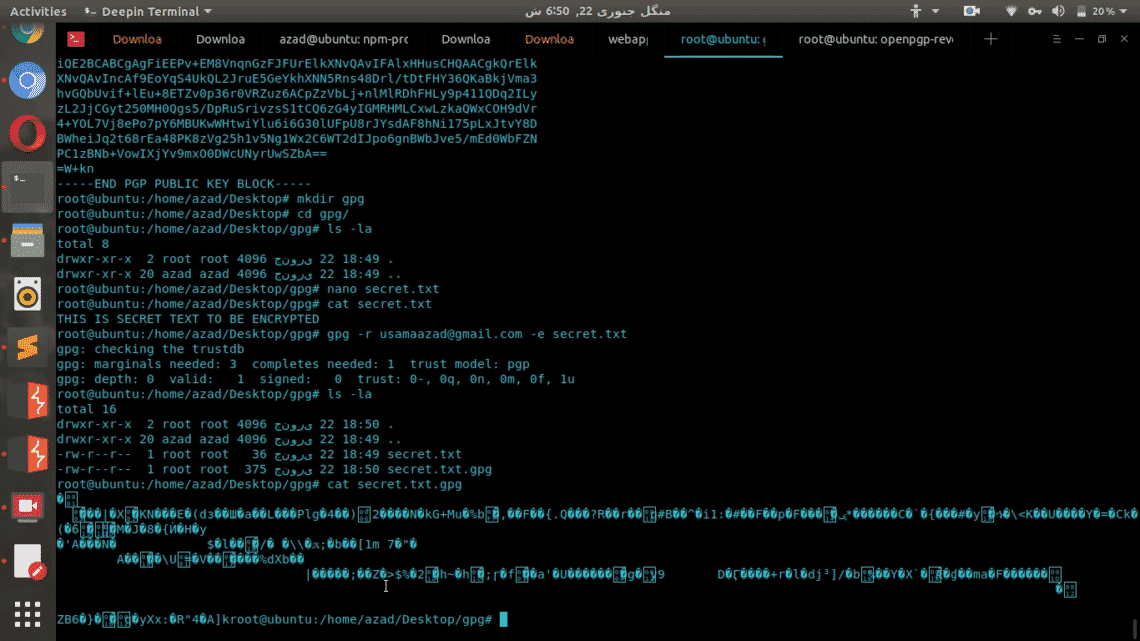
As you can see this encrypted file is whole new altered version of the original file which can’t be restored without the help of Private key.
Decryption
Now delete the original file secret.txt and then decrypt the gpg file using Private key
root@user:~/gpg# gpg -d secret.txt.gpg
It’ll ask you for a passphrase of Private key
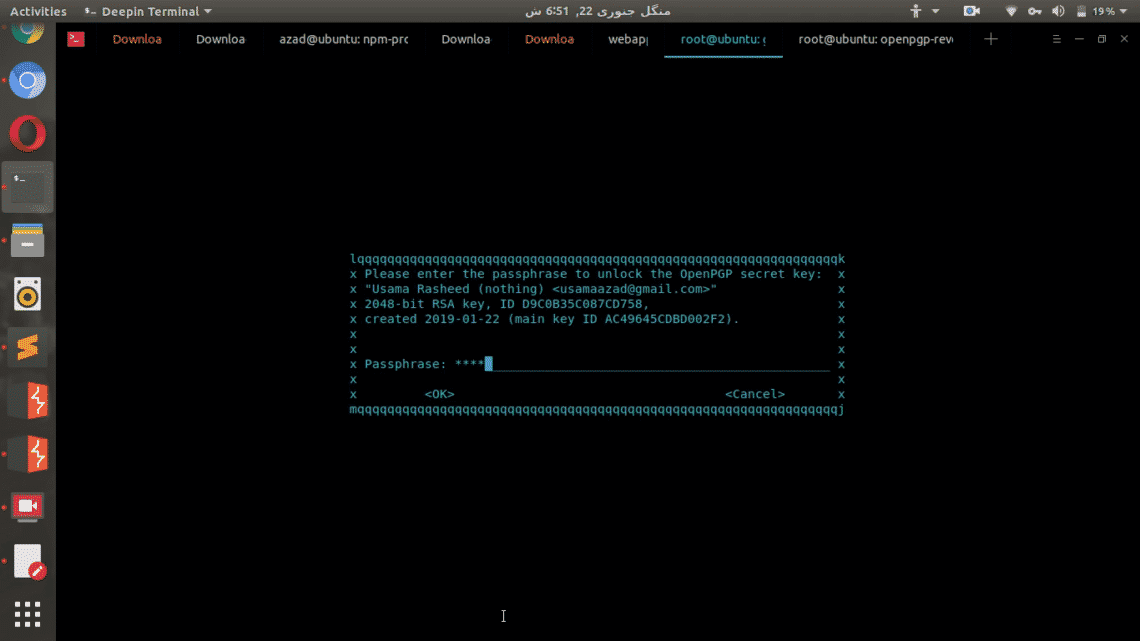
And then it’ll display the decrypted content of the file in the output.
Conclusion
There are variety of solutions available to implement different types of encryption techniques. Tools like TrueCrypt and VeraCrypt are used to encrypt hard drives and partitions but these aren’t efficient for general file or document encryption. GPG is a free and easy-to-use tool that can be used to encrypt secret files using secure asymmetric encryption which cannot be easily brute-forced.







