This tutorial shows how to install Wireshark on Debian 10 Buster and some basic functions but doesn’t go deeper into its usage, yet it is useful for previous Debian versions and based distributions such as Ubuntu and Mint. While Wireshark can be installed from repositories through apt or aptitude it’s sources and versions for different OS (Operating Systems) are available at https://www.wireshark.org/download.html.
Installing Wireshark on Debian 10 Buster
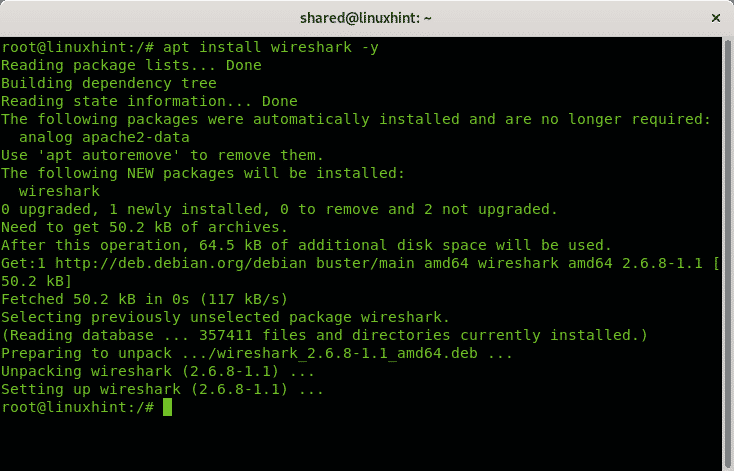
To install Wireshark on Debian 10 Buster or previous Debian versions run:
Wireshark basics
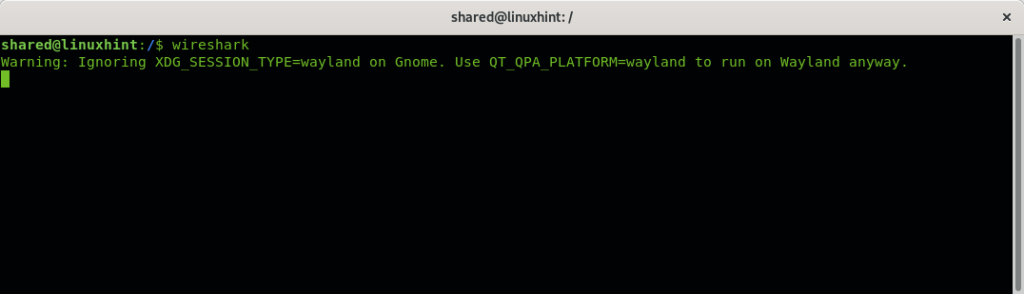
To launch Wireshark, on the terminal just run:
Note: don’t run Wireshark as root, execute it as unprivileged user only, you don’t need to be root user to capture packages over a network.
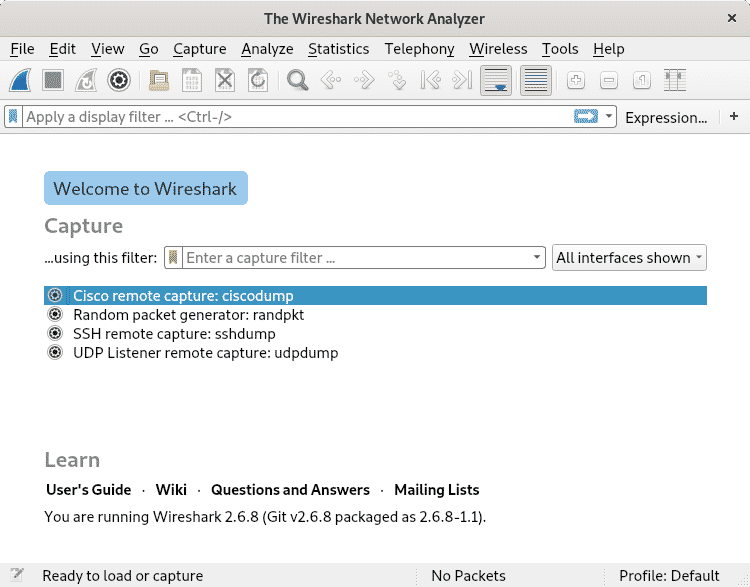
The following window will prompt
When launching Wireshark you’ll see two main menus:
And
On the first line you have menus with the following functionalities:
File: additionally to the usual options of any File menu, this one allows to export packets with different options, SSL session keys and objects.
Edit: this menu allows to copy and find specific content, to mark and ignore packets, manage timing options and packet comments. Through this menu you can also setup different configuration profiles and edit preferences such as visual preferences, mac and IP addresses resolutions and more.
View: this menu allows to configure different visual options such as menus, toolbars, zoom, expand and collapse among other estetic options.
Go: this menu contains options to browse packets.
Capture: from this menu you can launch Wireshark and configure options related to the capture of packages such as filters, name resolutions, interfaces and output options.
Analyze: from this menu you can enable and disable protocol dissectors, decode some packets and manage display filters.
Statistics: the Statistics menu allows to display the information in a variety of ways, including or discarding specific information.
Telephony: this menu contains options related to telephony such as VoIP, GSM, Osmux, RTP, SCTP and more.
Wireless: this menu contains options related to bluetooth and wlan.
Tools: here you’ll find options related to stateless firewall and Lua programming language.
Help: this menu contains helpful information on Wireshark.
The graphical menu below the explained above contains:
This button allows to launch Wireshark, it can also be found on the Capture menu described above.
This is the button to stop ongoing Wireshark analysis.
Here you can restart stopped capturing processes.
This button will open the Capture menu explained above.
This button will allow to open Capture files from previous sessions.
This button saves the current capture.
Close the current capture.
Reload a capture.
This button allows you to find packets.
This button allows to browse to the previous packet.
This button allows to browse to the next packet.
This allows to browse to a specific packet.
This button allows to move to the first packet.
This button allows to move to the last packet.
This button allows set automatic scroll to the last packet when Wireshark is working.
This button allows to color packets according to specified rules.
This button allows one to zoom in fonts.
This button allows to zoom out fonts.
This button allows to restore text font to the original size.
This button allows to resize columns to fit the content.
Conclusion:
Wireshark offers a considerable quantity of options to configure filters, timing and output formats, it has a very friendly and intuitive graphical environment but can be used from the command line too through TShark included in the package. It supports Ethernet, PPP, IEEE 802.11 and loopback network types. It can detect VoIP calls and in some cases can decode the content, it also allows to capture USB raw traffic, it allows to create plugins for dissecting new protocols and to filter Wireless connections if connected through a wired router or switch. Some interesting Wireshark alternatives include Ettercap, Kismet, EtherApe, SmartSniff, CloudShark and Omnipeek, additional alternatives can be found online.
Related articles
- How to Install and Use Wireshark on Ubuntu
- Wireshark Tutorial
- HTTP analysis using Wireshark
- How to use Wireshark Basics
- Install Wireshark 2.4.0 – Network Protocol Analyzer on Ubuntu
- Packet Filter Analysis for ICMP in Wireshark
- UDP Wireshark Analysis
- OSI Network Layer Analysis via Wireshark
- Driftnet on Debian: Sniffing images within a network