- Vulnerability Assessment and Pentesting
- IDS signature development
- Exploit development and research
The newest major Metasploit release has moved its core to an all Ruby programming base. Metasploit-framework uses Ruby as its core programming language because Ruby is a powerful interpreted language. The Metasploit Project is very famous because of its anti-forensic and detection evasion features.
Metasploit generally offers a community and open source version of Metasploit Framework but it also has commercial versions like Metasploit Pro and Metasploit Express. It also has a shellcode database, these shellcodes can be used to perform reverse shell to the the attacker’s machine.
Like other similar products like Canvas or Core Impact and other commercial security products, Metasploit-Framework can be used to check the security of computer systems or to break into network and systems. Similar to many other security tools, Metasploit Framework can be used for both authorized and unauthorized activities.
Follow below steps to install Metasploit Framework in your Ubuntu OS
Installation
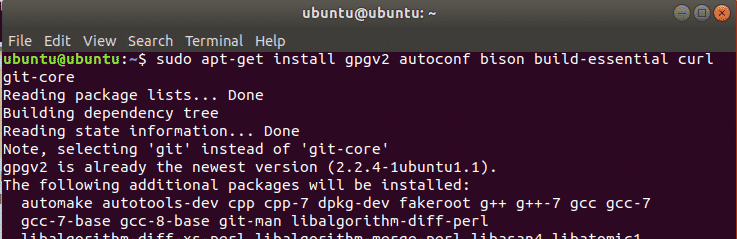
Metasploit Frame is easy to install and and has a few dependencies. Before installing, make sure to update your Ubuntu
$ sudo apt-get upgrade
Installing dependencies
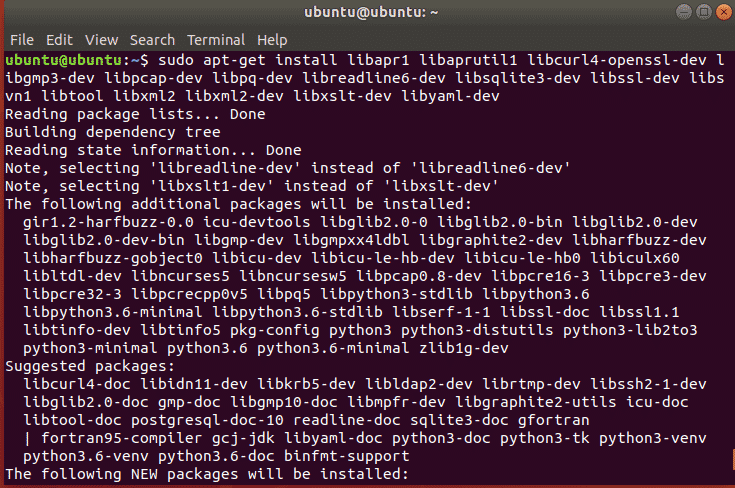
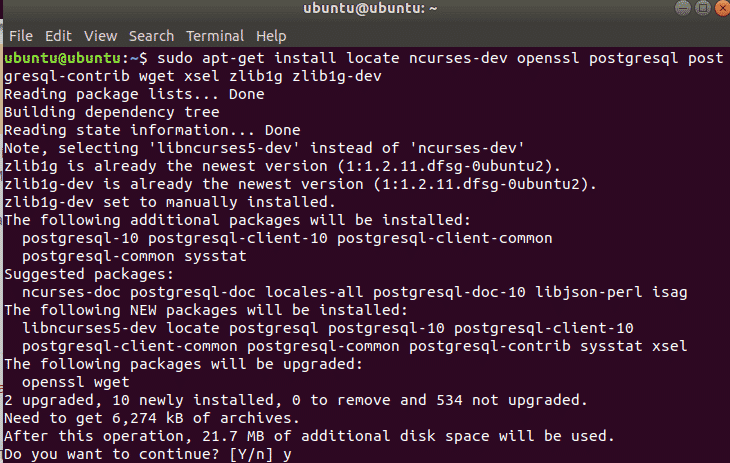
Before installing you need to install following dependencies using apt command
git-corelibapr1 postgresql libaprutil1 libcurl4openssl-dev libgmp3-dev libpcap-dev
openssl libpq-dev libreadline6-dev libsqlite3-dev libssl-dev locate libsvn1 libtool
libxml2 libxml2-dev libxslt-dev wget libyaml-dev ncurses-dev postgresql-contrib xsel
zlib1g zlib1g-dev
Installing
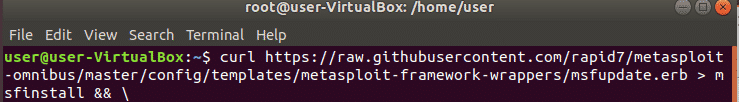
curl is used to transfer files from remote computers and supports a lot of protocols, we will use it to download metasploit framework code.
omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb
> msfinstall &&
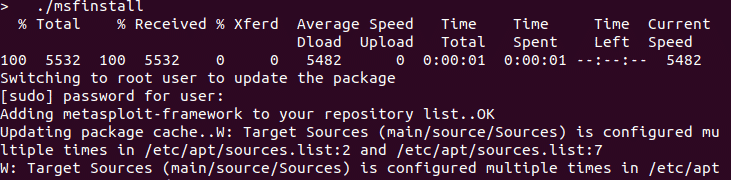
Then change permissions of the executable code using chmod command then run it
owner = Read & Write (rw-)
group = Read (r–)
other = None (—)
Ownership:
owner = root
group = shadow
$ chmod 755 msfinstall
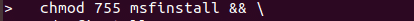
Metasploit Interfaces
Metasploit Framework has a web interface, GUI interface (Armitage and Cobal Strike) and Command Line interfaces (msfcli, msfconsole). It also offers APIs like msgrpc to control Metasploit remotely or to use it along with some some scripting language for automation purposes.
It also has some other tools and features that can generate shell codes and payloads and combine them with other legitimate executables.
Msfconsole is a powerful Command line interface of Metasploit. To run it, first start postgresql service, Type
ubuntu@ubuntu:~$ sudo msfconsole
Metasploit Manual
Common commands for Metasploit from the Manual
help (or ‘?’) – shows the available commands in msfconsole
show exploits – shows the exploits you can run (in our case here, the ms05_039_pnp exploit)
show payloads – shows the various payload options you can execute on the exploited system such as spawn a command shell, uploading programs to run, etc. (in our case here, the win32_reverse exploit)
info exploit [exploit name] – shows a description of a specific exploit name along with its various options and requirements (ex. info exploit ms05_039_pnp shows information on that specific attack)
info payload [payload name] – shows a description of a specific payload name along with its various options and requirements (ex. info payload win32_reverse shows information on spawning a command shell)
use [exploit name] – instructs msfconsole to enter into a specific exploit’s environment (ex. use ms05_039_pnp will bring up the command prompt ms05_039_pnp > for this specific exploit
show options – shows the various parameters for the specific exploit you’re working with
show payloads – shows the payloads compatible with the specific exploit you’re working with
set PAYLOAD – allows you to set the specific payload for your exploit (in this example, set PAYLOAD win32_reverse)
show targets – shows the available target OSs and applications that can be exploited
set TARGET – allows you to select your specific target OS/application (in this example, I’ll use set TARGET 0 to for all English versions of Windows 2000)
set RHOST – allows you to set your target host’s IP address (in this example, set RHOST 10.0.0.200)
set LHOST – allows you to set the local host’s IP address for the reverse communications needed to open the reverse command shell (in this example, set LHOST 10.0.0.201)
back – allows you to exit the current exploit environment you’ve loaded and go back to the main msfconsole prompt
Conclusion
Metasploit is a very useful framework that is used by Penetration testers and vulnerability researchers. Some other commercial tools offer similar functionality but Metasploit is popular due to its cross-platform support and easy-to-use GUI and CLI interfaces. This is particularly make for Penetration testers and Red Teamers but anyone can use this to secure their home or company’s network. If you are interested in learning Metasploit, here is a great free resource.