RDDOS attack takes advantage of the lack of reliability of the UDP protocol which does not establish a connection previously to the packet transference. Therefore forging a source IP address is pretty easy, this attack consists of forging the victim’s IP address when sending packets to vulnerable UDP services exploiting their bandwidth by prompting them to reply to the victim’s IP address, that’s RDDOS.
Some of the vulnerable services may include:
- CLDAP (Connection-less Lightweight Directory Access Protocol)
- NetBIOS
- Character Generator Protocol (CharGEN)
- SSDP(Simple Service Discovery Protocol)
- TFTP (Trivial File Transfer Protocol)
- DNS (Domain Name System)
- NTP (Network Time Protocol)
- SNMPv2 (Simple Network Management Protocol version 2)
- RPC (Portmap/Remote Procedure Call )
- QOTD (Quote of the Day)
- mDNS (Multicast Domain Name System ),
- Steam Protocol
- Routing Information Protocol version 1 (RIPv1),
- Lightweight Directory Access Protocol (LDAP)
- Memcached,
- Web Services Dynamic Discovery (WS-Discovery).
Nmap Scan Specific UDP port
By default Nmap omits UDP scan, it can be enabled by adding the Nmap flag -sU. As listed above by ignoring UDP ports known vulnerabilities may remain ignored to the user. Nmap outputs for UDP scan may be open, open|filtered, closed and filtered.
open: UDP response.
open|filtered: no response.
closed: ICMP port unreachable error code 3.
filtered: Other ICMP unreachable errors (type 3, code 1, 2, 9, 10 or 13)
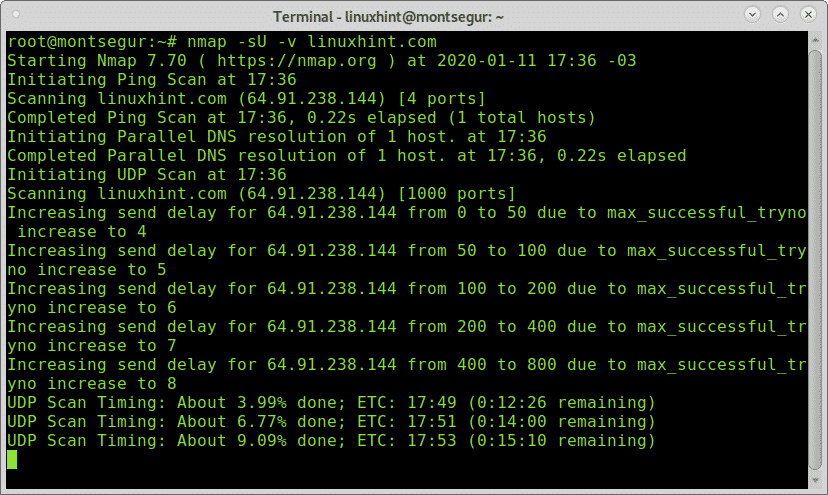
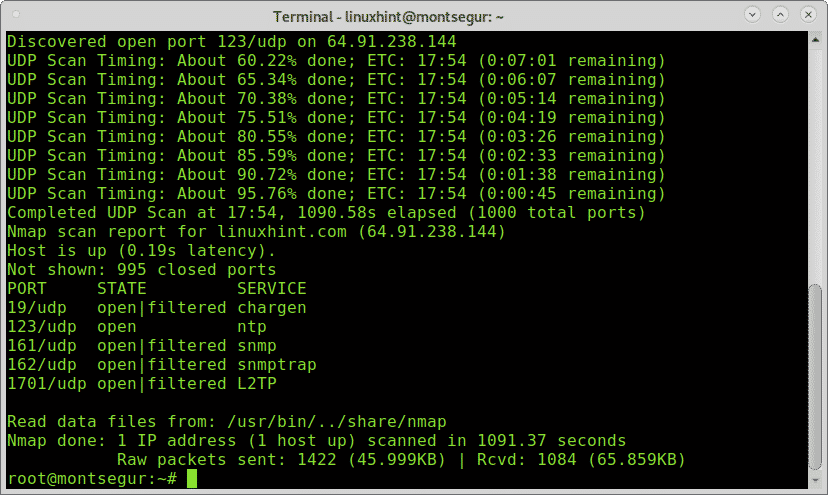
The following example shows a simple UDP scan without additional flag other than the UDP specification and verbosity to see the process:
The UDP scan above resulted in open|filtered and open results. The meaning of open|filtered is Nmap can’t distinguish between open and filtered ports because like filtered ports, open ports are unlikely to send responses. Contrary to the open|filtered, the open result means the specified port sent a response.
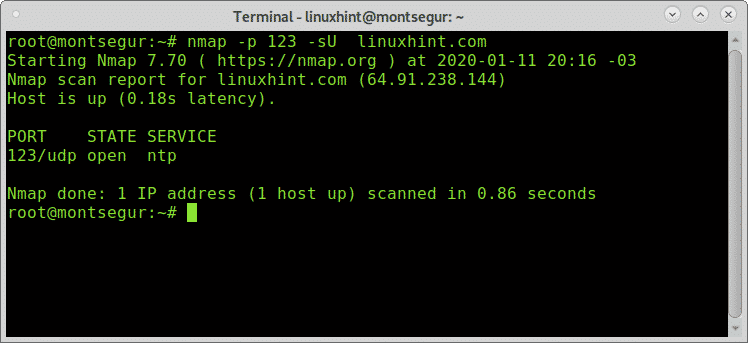
To use Nmap to scan a specific port use the -p<port> flag to define the port followed by the -sU flag to enable UDP scan before specifying the target, to scan LinuxHint for the 123 UDP NTP port run:
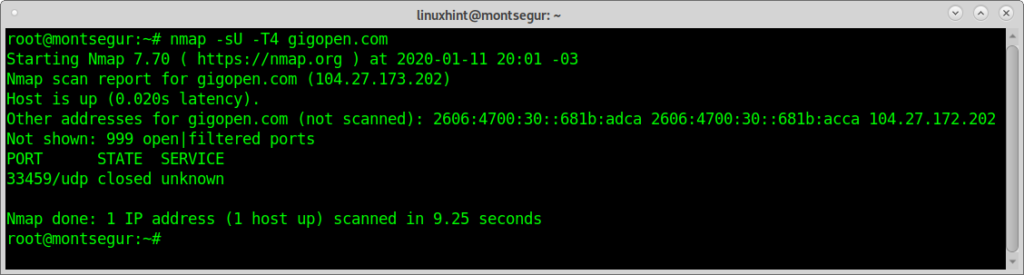
The following example is an aggressive scan against https://gigopen.com
Note: for additional information on the scan intensity with the flag -T4 check https://books.google.com.ar/books?id=iOAQBgAAQBAJ&pg=PA106&lpg=PA106&d.
UDP scans make the scanning task extremely slow, there are some flags which can help to improve the scan speed. The -F (Fast), –version-intensity flags are an example.
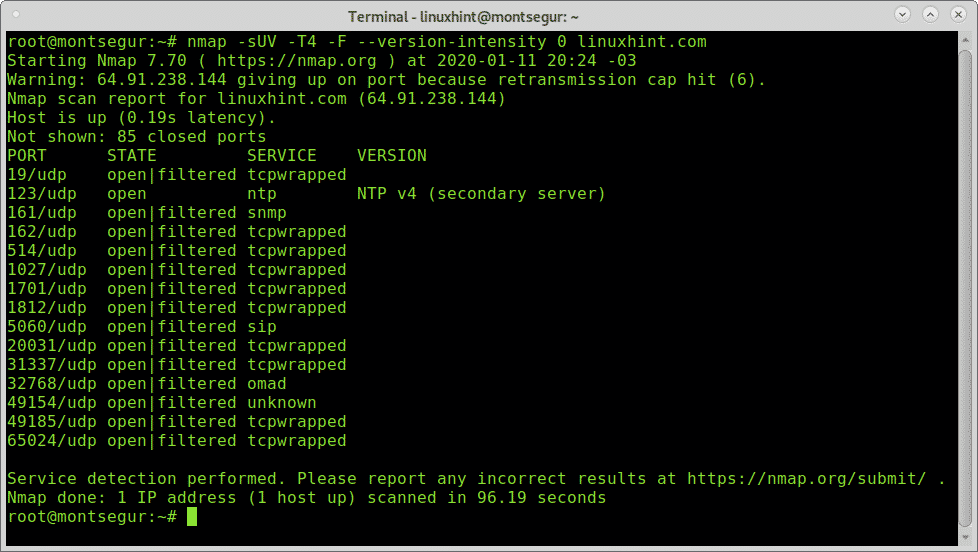
The following example shows a scan speed increase by adding these flags when scanning LinuxHint.
Speeding up a UDP scan with Nmap:
As you see the scan was one in 96.19 seconds against 1091.37 in the first simple sample.
You can also speed up by limiting retries and skipping host discovery and host resolution as in the next example:
Scanning for RDDOS or Reflective Denial Of Service candidates:
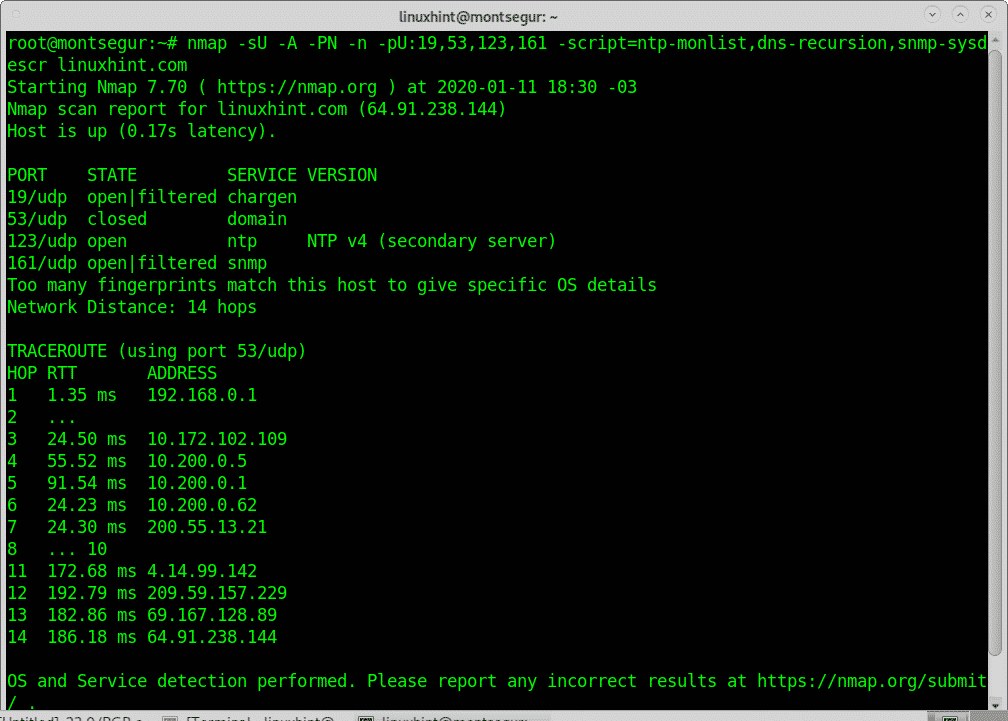
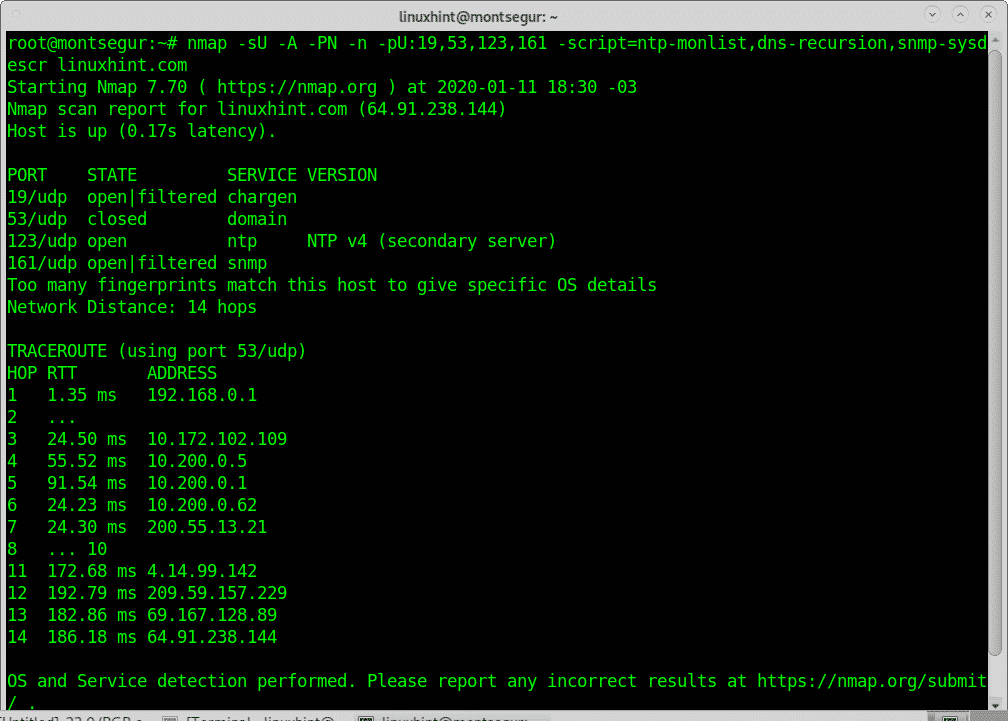
The following command includes the NSE (Nmap Scripting Engine) scripts ntp-monlist, dns-recursion and snmp-sysdescr to check for targets vulnerable to Reflective Denial of Service Attacks candidates to exploit their bandwidth. In the following example the scan is launched against a single specific target (linuxhint.com):
dns-recursion,snmp-sysdescr linuxhint.com
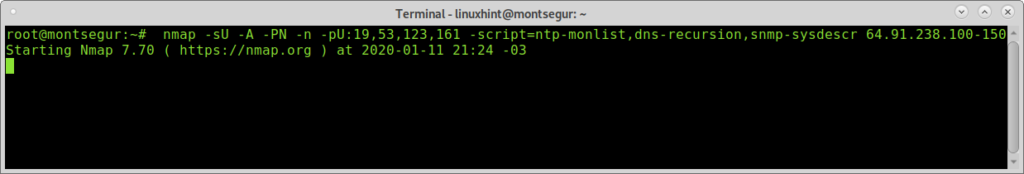
The following example scans 50 hosts ranging from 64.91.238.100 to 64.91.238.150, 50 hosts from the last octet, defining the range with an hyphen:
snmp-sysdescr 64.91.238.100-150
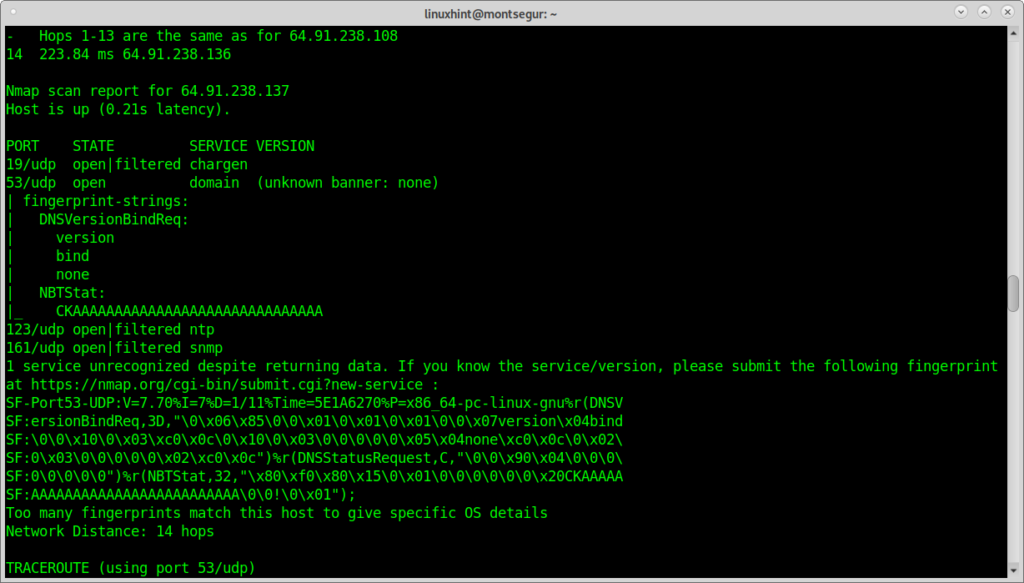
And the output of a system we can use for a reflective attack seems like:
Brief Intro to the UDP Protocol
The UDP (User Datagram Protocol) protocol is part of the Internet Protocol Suite, it is faster but unreliable when compared against TCP (Transmission Control Protocol).
Why is the UDP Protocol faster than TCP?
The TCP protocol establishes a connection to send packets, the connection establishment process is called handshake. It was clearly explained at Nmap Stealth Scan:
“Usually when two devices connect, connections are established through a process called three way handshake which consists of 3 initial interactions: first of a connection request by the client or device requesting the connection, second by a confirmation by the device to which the connection is requested and in third place a final confirmation from the device which requested the connection, something like:
-“hey, can you hear me?, can we meet?” (SYN packet requesting synchronization)
-”Hi!, I see you!, we can meet” (Where “I see you” is an ACK packet, “we can meet” a SYN packet)
-”Great!” (ACK packet)”
Source: https://linuxhint.com/nmap_stealth_scan/
Contrary to this the UDP protocol sends the packets without previous communication with the destination, making the packets transference faster since they don’t need to wait to be sent. It is a minimalist protocol without retransmission delays for resending missing data, the protocol by choice when high speed is needed, such as VoIP, streaming, gaming, etc. This protocol lacks reliability and it is only used when packet loss isn’t fatal.
The UDP header contains information on source port, destination port, checksum and size.
I hope you found this tutorial on Nmap to scan UDP ports useful. Keep following LinuxHint for more tips and updates on Linux and networking.